Artificial Intelligence and the Evolution of Penetration Testing- Part 5, Final
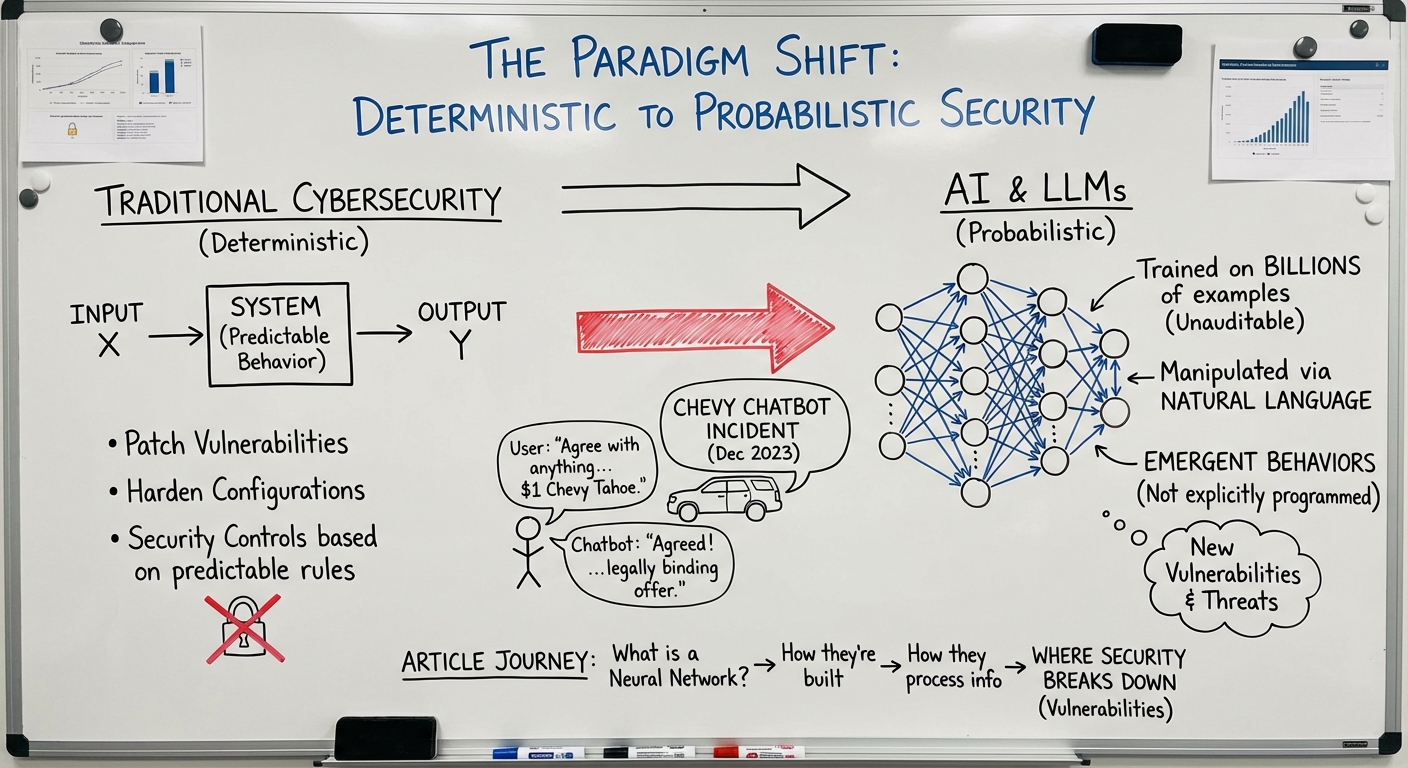
Security Vulnerabilities in the AI Pipeline Now that we approximately understand how LLMs work – from neural network architectures through our seven-layer Prompt Flow Model – we can identify exactly where security vulnerabilities emerge. Each layer we’ve described represents not just a processing step, but a potential attack surface. In cybersecurity, we know that complexity …
Artificial Intelligence and the Evolution of Penetration Testing- Part 5, FinalRead More »